Networking Security Challenges
Network security is no longer confined to the data center because edges of the network have expanded well beyond. Today, more than ever, cybersecurity professionals are contending with an entirely new type of network and an entirely new set of security needs. They need a new way to keep users, data, and devices safe from threats with more remote workers, more roaming devices to protect. The widespread use of cloud-based apps or services makes them vulnerable to breaches. Even a lot of breaches take place inside approved trusted connections or sometimes employees are in an understandable hurry to do things quickly, cut, copy, paste, share, and shift sensitive data to places where your organization doesn’t want it.
With these changes, zone defense is no longer sufficient, and the chance of successful attacks or compliance violations rises. “As per a survey by Cisco, 64% of organizations reported that network security at the edge has become more difficult than it was 2 years ago. And, 26% said that the number of disparate network security tools was a major contributor to this increased difficulty. These point products are generating thousands of alerts, but many go untouched. In fact, 52% of daily alerts are not investigated. ” According to research published by IBM and Ponemon, the average total cost of a data breach is $3.86 million.
Ransomware attacks have been on the rise in the Covid-19 situations, so much that they have become the biggest single money earner for cybercriminals. Group-IB estimated that the number of Ransomware attacks grew by 150% in 2020 and that the average ransomware demand has increased more than 200% to $170,000.
Security Redefined With SASE
By the above discussions, it is clear that enterprises require security that can-
- To minimize the complexity of your security architecture to make work easier for both users and the security team.
- To provide users — with many permutations of locations device, users identity — with fast, responsive interactions with their apps so they can get the full benefits of the cloud.
- To manage risks to your business continuously by being able to easily see and quickly address potentially risky activity involving company data and users
To address all the issues, architecture has been developed which is known as SASE architecture. SASE is the simple word that can be described as the convergence of WAN, and network security services like CASB, FWaaS, and Zero Trust, into a single, cloud-delivered service model.
According to Gartner, “SASE capabilities are delivered as a service-based upon the identity of the entity, real-time context, enterprise security/compliance policies and continuous assessment of risk/trust throughout the sessions. Identities of entities can be associated with people, groups of people (branch offices), devices, applications, services, IoT systems or edge computing locations.”
SASE has unique computing and performance requirements that make it possible to support a microservices-based architecture designed for security workloads. So, SASE dramatically simplifies and improves the quality of your security and your network connectivity. When SASE is done right, all these things happen in real-time, including continuous risk management. By moving security services out of your data center and into the cloud, closer to both your points of vulnerability and your users, you gain greater visibility and firmer control over what’s going on, with whom, at all times.
The Fundamental Components of the SASE are
SWG (Secure Web Gateways):
A secure Web gateway is a solution that filters unwanted software/malware from Web/Internet traffic and enforces corporate and regulatory policies.
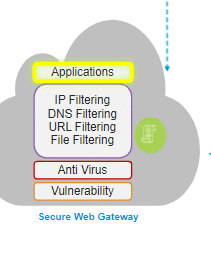
The SWG consists of a few components like URL filtering, malicious-code detection and filtering, and application controls for popular Web-based applications, etc. These all services are applied in coordination with the many new services that work together to inspect deep inside your SaaS and web traffic, gain that super-rich understanding, and enforce context-based security policies.
SWG generally focuses on:
- Website and content restrictions with unified security policies
- Ability to inspect HTTPS traffic through SSL Decryption
- Network visibility, monitoring, and reporting
- Applications controls for enterprise and internet hosted apps
- Web activity approach for IP filtering DNS, URL, File, etc
- SSL encryption and decryption to analyze malware and bloatware on the internet using antivirus
- Security approach to use IDP engine to block all L3, L4, or L7 based attacks
All the services provided by the SWG above together can be named FWaaS (Firewall as a Service)
Zero Trust Network Access (ZTNA):
According to Gartner “Zero trust network access (ZTNA) is a product or service that creates an identity- and context-based, logical access boundary around an application or set of applications. The applications are hidden from discovery, and access is restricted via a trusted broker to a set of named entities. The broker verifies the identity, context, and policy adherence of the specified participants before allowing access and prohibits lateral movement elsewhere in the network. This removes application assets from public visibility and significantly reduces the surface area for attack.”
The feature of ZTNA are:
- It completely isolates the act of providing application access to the network. This isolation reduces risks to the network, such as infection by authorized compromised devices.
- It makes outbound-only connections ensuring both network and application infrastructure are made invisible to unauthorized users. IPs are never exposed to the internet and keep it away from Shadow IT.
- It ensures users are authorized, application access is granted on a one-to-one basis and Authorized users have access only to particular applications Instead of full access to the network.
Even from an architectural perspective, it works fundamentally differently from network-centric solutions. These are most often 100% software-defined that eliminate the enterprise’s overhead of managing appliances. It is also known as Software Defined Perimeter.
Cloud Access Security Broker (CASB):
Threats can enter through many directions, eg. A trusted user with bad intentions can bypass the security roles because they are valid, trusted users with valid credentials, or a trusted user falls to phishing attacks by downloading malware to their laptops and mobile devices. And to address shadow IT functions CASB (cloud access security blocker) is introduced.
This is done through a three-step process:
- Discovery: The CASB solution uses auto-discovery of applications via cloud services and gateways. it also identifies the users accessing the data.
- Classification: The CASB determines the risk level associated with each discovered application, calculates risk level scores based on different aspects like application classification, data types, and usage of data by the user.
- Adaptive Access Control: Enforces Contextual Security control policies based on data sensitivity, risk scores, and user/devices.
- Data Security: Identifies potential misuse of data via DLP
- User Entity and Behaviour Analysis: Discover normal vs suspicious activities behaviors
Identifies potential misuse of data via DLP, uses data encryption, and user audits. Some common use cases of CASB are as follows-
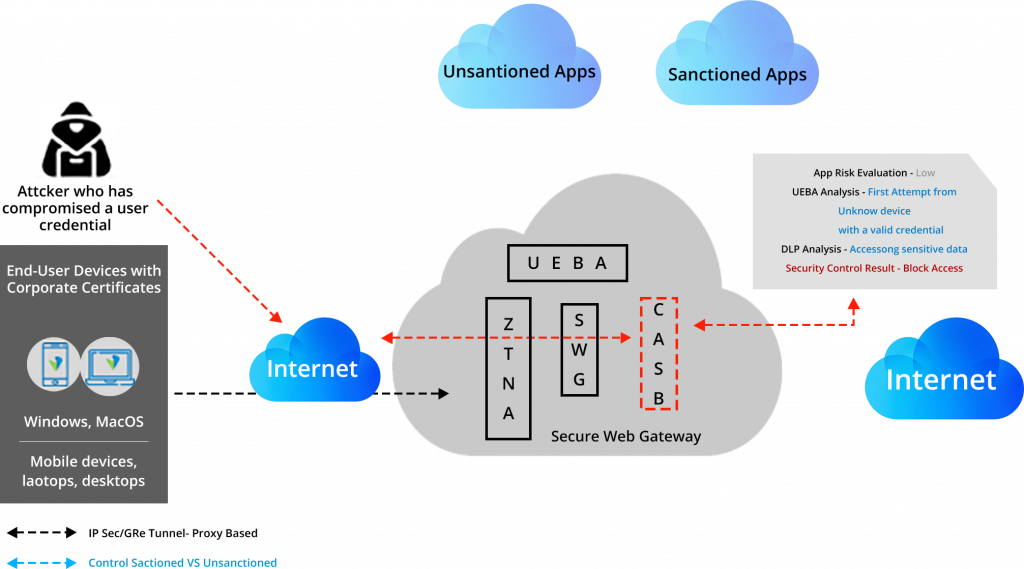
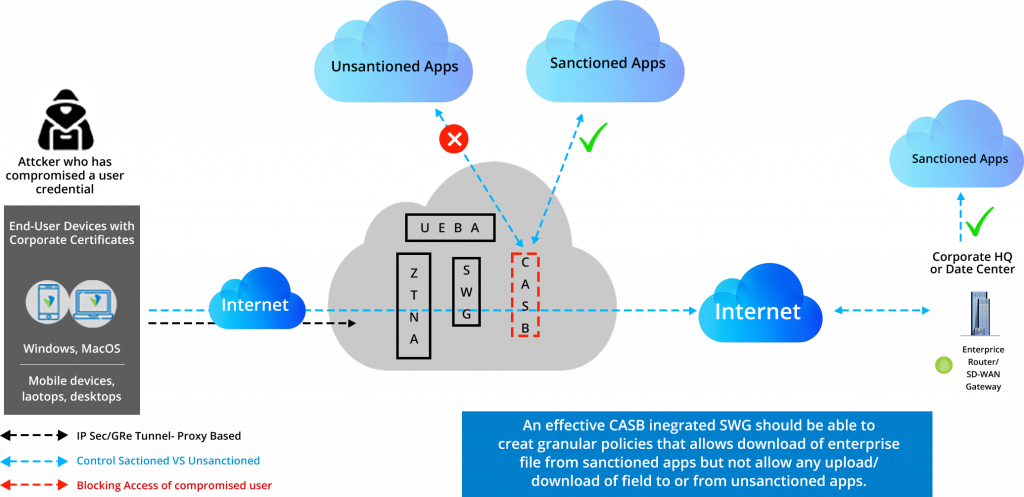
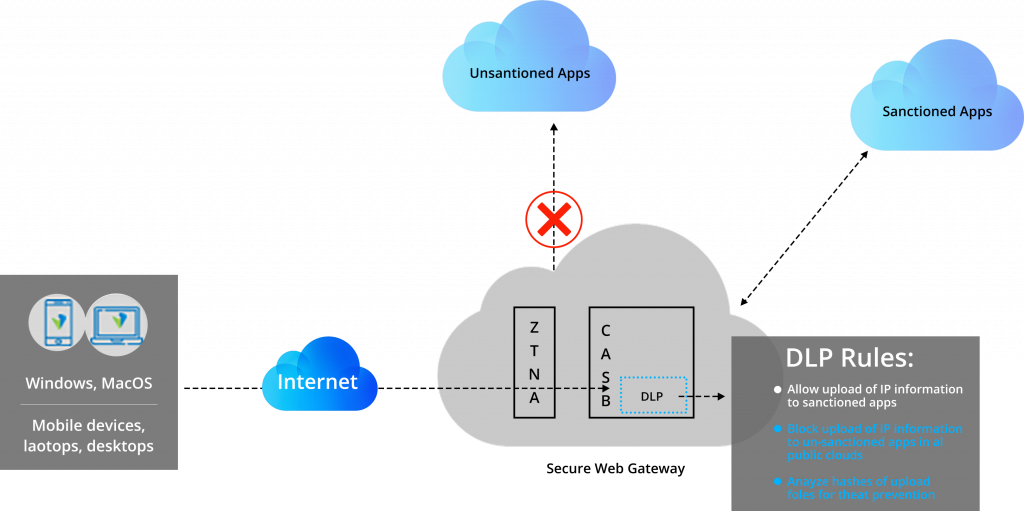
Data Loss Prevention (DLP):
As per Gartner’s definition of DLP (Data Loss Prevention), “it is a technology that performs both content inspection and contextual analysis of data sent via messaging applications such as email and instant messaging, in motion over the network, in use on a managed endpoint device, and at rest in on-premises file servers or in cloud applications and cloud storage. These solutions execute responses based on policy and rules defined to address the risk of inadvertent or accidental leaks or exposure of sensitive data outside authorized channels.”
The one use case has been shown below-
Lets the user have IP content on the servers. The content is allowed only to the sanctioned applications, not the unsanctioned applications.